Identify and resolve misconfigured permissions before they derail your AI rollout
Redactive Permissions Assurance uses AI-native analysis to understand and protect your data, ensuring that AI applications, agents -- and the employees using them -- only have access to the information they're supposed to.
In the AI-era, data access debt has become a critical threat
Security teams are managing an ever-expanding web of permission structures across countless applications and documents, resulting in widespread misconfigured permissions where 'security by obscurity' is an accepted norm.
We call this data access debt, and it's a security threat that's blocking AI initiatives before they ever reach production.
Redactive Permissions Assurance identifies and fixes misconfigured permissions, solving your data access debt at scale, so you can embrace AI without the threat of data leaks.
How It Works: Redactive Permissions Assurance
Learn how Permissions Assurance solves data access debt at scale, uplifts your organization's data security posture, and ensures secure AI access
Understand your true risk exposure with semantic, document-level access analysis
Redactive leverages AI to understand the contextual meaning of your unstructured data, alerting you to inappropriate document-level access that rules-based solutions fail to identify.
Map and control permissions at the document-level, rather than the application-level
Detect misconfigured permissions based on the meaning of the content within your documents
Automatically detect anomalous permissions across users, groups, and documents
Continuously and automatically remediate data access risks
Redactive ensures you never waste time manually managing data access again, allowing your security and data governance teams to focus on more strategic initiatives.
Automatically correct misconfigured permissions in minutes—not months
Put data access control on autopilot with automated, real-time remediation
Intelligently route edge cases to the correct data owners for review
Redactive is birthright software that gives us confidence in our knowledge base permissions.
Multi-billion dollar pension fund

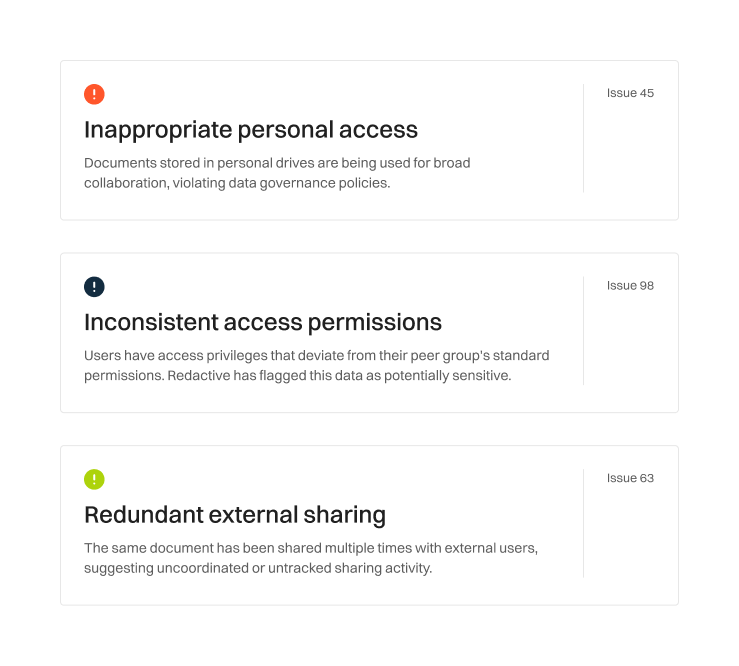
Unblock AI initiatives, knowing your data is truly secure
Misconfigured permissions are on every organization's risk register, and AI threatens to turn them into data leaks. Redactive Permissions Assurance secures your AI rollout by enabling you to:
Size the risk AI presents by detecting inappropriate data access that was previously hidden by obscurity
Continuously and automatically correct misconfigured permissions at the source, ensuring your data is always AI-ready
Get prioritized recommendations for vulnerabilities that require human attention

Fill the gap in your AI data security stack
AI has exposed a critical gap in most organizations' data security strategies -- widespread misconfigured permissions.
Redactive Permissions Assurance elevates your existing data security capabilities by identifying and correcting access issues at the sentence-, image-, and chunk-level using AI-native analysis to identify access anomalies -- solving a challenge that was previously impossible to solve.
By complementing your current tools and leveraging your existing classifications, Redactive Permissions Assurance revolutionizes your approach to data security, giving you unparalleled visibility into the vulnerabilities that AI will take advantage of.
Is data access debt blocking your AI rollout?
Learn how Redactive enables security and engineering teams to gain precise, contextual control over what data employees, agents, and AI applications can access—ensuring unauthorized data exposure is prevented.

Frequently Asked Questions
Does Redactive replace an LDAP / DPSM?
No, Redactive complements your existing data security tools, solving a new data security challenge that AI is exposing whilst elevating your overall security posture.
Application-level security and traditional access controls are insufficient in the face of AI. While existing tools like Data Security Posture Management (DSPM) solutions excel at discovery and classification, they fall short of solving the fundamental access challenge. LDAP systems, while providing group-level control, can't deliver the granular visibility that AI demands.
Redactive's AI Data Security platform focuses on identifying and correcting improper fine-grained data access at the sentence-, image-, or chunk-level, using AI-native analysis to identify access anomalies -- solving a challenge that was previously impossible to solve, and enabling organizations to secure their data in anticipation of how AI will surface it.
Where does Redactive fit into an AI implementation?
Redactive sits between your knowledge bases and your AI tooling (think Copilot, Glean, or your custom LLM solution) and acts as a pre-retrieval guardrail to ensure your AI application's responses only contain the data that the end user should have access to.
Redactive leverages the existing rules and classifications from your SSO, LDAP, and DSPM, but goes a step further, adding a fine-grained layer of security to your data by using semantic analysis, granular access management, and context-aware permissions to protect enterprise data before it reaches any LLM system, securing data access at the infrastructure level rather than relying on LLM-level controls.
Don't AI tools already respect data access controls / existing permissions?
Yes, they do. But that only protects your data if access controls are in a perfect state to begin with.
The reality is that for most organizations, data access controls are in a messy state. Most have a huge amount of data access debt, where misconfigured permissions at the document-level are rife, and fine-grained access controls are impossible for security teams to fix at scale.
This means that whilst Copilot, Glean, or any other AI tool may respect existing permissions boundaries, the access controls themselves are inherently flawed, and many employees have access to data that they shouldn't have.
Of course, before AI it was unlikely that employees would come across this data, which is often buried deep in an organization's knowledge bases and difficult for humans to find. However, AI applications will find and return this information in seconds, exposing data that the user should not have access to. For that reason, it's imperative that organizations employ an AI Data Security solution like Redactive to safely activate AI across their data without compromising on security.